Contents
The IT Security Act 2.0 (IT-SiG 2.0) - What is important now?

The IT-SiG 2.0 is intended to tighten the defense mechanisms and obligations to provide evidence. A country like the Federal Republic of Germany can hardly exist without functioning IT systems. In practice, however, this fact is often ignored. Cyber attacks on companies, authorities and other institutions are reported on an almost weekly basis. More and more often with success and often with considerable damage.
The German government wanted to counter this and has revised the IT Security Act (IT-SiG 1.0). Version 2.0 (IT-SiG 2.0) is intended to provide the framework for strengthening IT security and adapting it to current and future challenges. The IT Security Act 2.0 has been in force since May 28, 2021 and also includes rules for companies that were not previously affected. Companies had two years to adapt to the new rules. From May 2023, the stricter regulations will now apply to the affected companies and institutions. This legally mandated security also provides for massive changes to security standards. Previously, the requirements were only implicitly specified through the introduction and establishment of an ISMS in accordance with ISO 27001 or the B3S industry standards.
Who is affected by IT-SiG 2.0?
The group of affected parties has been significantly expanded and affects not only the so-called KRITIS operators, but also other companies and organizations that have been classified as critical or are in the supply chain of critical companies. Specifically, companies from the energy, water, food and ITC sectors were previously primarily affected by the IT Security Act; with the IT Security Act 2.0, waste disposal companies and companies with a special public interest in general are also included.
Who falls under KRITIS operators?
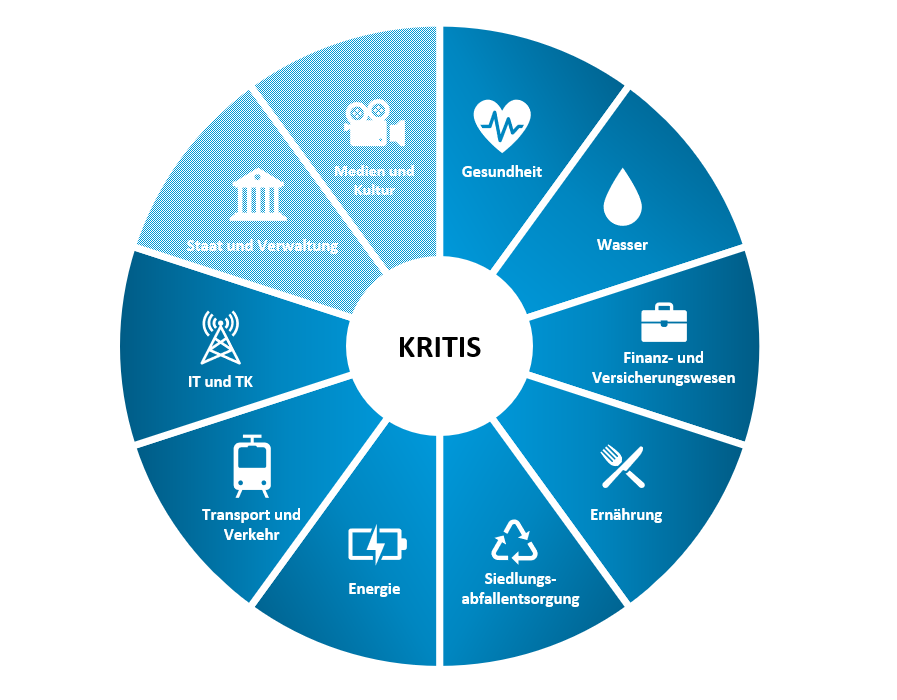
- Water: wastewater disposal, water supply
- Energy: electricity, district heating, gas, mineral oil
- Nutrition: food industry, food trade
- Finance and insurance: Banks, stock exchanges, financial services, insurance
- Health: medicines and vaccines, laboratories, medical care
- Information Technology and Telecommunications: Information Technology, Telecommunications
- Media and culture: printed and electronic press, cultural assets, broadcasting, symbolic buildings
- State and administration: judiciary, emergency and rescue services, parliament, government and administration
- Transport and traffic: inland shipping, logistics, aviation, rail transport, maritime shipping, road transport
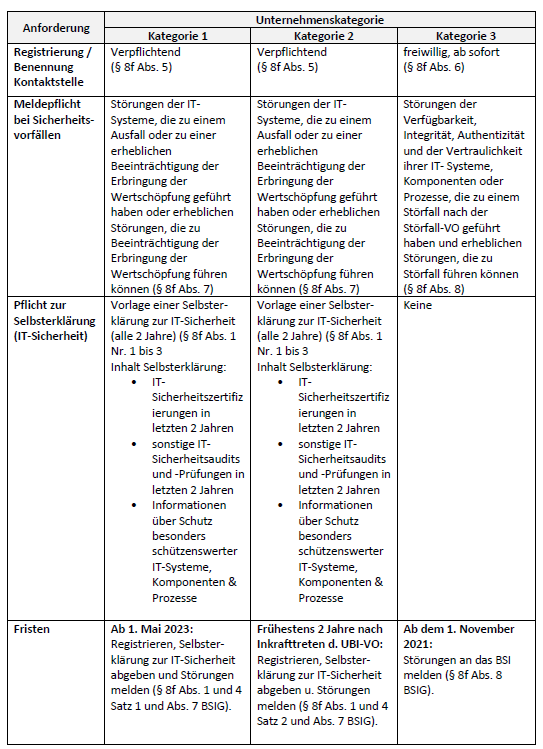
Who is a company in the special public interest (UBI)?
Addition of the category "Companies in the special public interest" This new IT-Sig 2.0 category now also includes the following companies:
- Category 1 UBI: This includes companies that are active in the field of weapons, ammunition and armaments or in the field of products with IT security functions for processing classified government information.
- Category 2 UBI: Companies of particular economic importance (these could be DAX companies, for example)
- Category 3 UBI: Companies that are subject to the Hazardous Incident Ordinance (StöV), for example companies and laboratories that deal with chemical substances.
BSI requirements for "UBI"
BSI with new tasks and competencies
In order to enforce the IT Security Act 2.0, the BSI (Federal Office for Information Security) in particular was granted new powers and tasks.
- This concerns detection, i.e. the active search for security vulnerabilities and the defense against cyber attacks. To this end, the authority will in future be able to request inventory data from telecommunications providers and order the rectification of identified security vulnerabilities.
- The BSI can also define and monitor security standards in information technology for federal authorities. Its authority over mobile network operators has also been extended. For example, the BSI may prohibit the use of questionable components if their operation undermines security standards. Network operators must prove to the BSI that they meet their security requirements and have critical components certified.
- As the national authority for cyber security certification, the BSI is also responsible for this and must implement the European standards within this framework.
Digital consumer protection is also a new task of the BSI
The BSI's future list of tasks also includes digital consumer protection. This means that the authority will be the point of contact for consumers when it comes to IT security. Among other things, it will introduce a standardized IT security label to make IT security more visible. The aim of these measures is to identify and close security gaps as quickly as possible and thus guarantee cyber security in Germany.
The new requirements of the IT-SiG 2.0
How can KRITIS companies meet the requirements of IT-Sig 2.0?
The IT Security Act 2.0 has significantly expanded the requirements for companies to ensure their IT security. Minimum standards for critical infrastructures must be ensured, for example by operating a Security Operations Center (S OC) to detect cyber attacks effectively and, above all, at an early stage. In addition to the SOC, there are also other options for detecting attacks, such as a SIEM . With such detection systems, companies will have to prove in future that they have functioning technical and organizational processes in place to ensure reliable detection of attempted attacks. Companies can demonstrate compliance with these standards through audits and certifications, but are obliged to provide information to the BSI in the event of queries. Companies are also required to register critical infrastructure with the BSI. These standards must be ensured on a permanent basis. Companies must therefore keep the necessary technical equipment up to date. Companies must prove compliance with these requirements to the BSI every two years.
Threat detection and defense processes
If threats to the company's own IT systems are detected, they must not only be reported, but a concrete process plan must also be set in motion that includes specific instructions for action and defines clear responsibilities in the Security Operations Center. In order to meet this requirement, a head should be appointed for the SOC, as well as a response team for the operational defense against cyber attacks. However, the tasks of the SOC team begin with detection, in which a security incident can be recognized based on logs, access patterns or other indicators. Such an incident must then be classified so that the appropriate measures can be initiated. The experience gained should be evaluated for the future and ideally the processes should be further optimized or improved as a result. Tools such as the automated pentest software from Guardian360 can provide additional support here.
Certificates for system components
Critical infrastructure companies in particular are already familiar with this approach. To ensure cyber security in Germany, they will also have to use security-relevant system components from trustworthy, certified manufacturers in the future. The systems must also be able to detect and ward off attacks. The IT-SiG 2.0 clearly focuses on the use of critical components in vulnerable IT systems. These components may only be used if they have been registered with the BSI and the manufacturer has provided certification and a guarantee declaration. This guarantee covers the entire supply chain and thus extends the circle of affected companies. The IT Security Act 2.0 expressly empowers the BSI to carry out inspections. The companies concerned must provide all documents that enable the authority to assess compliance. This also includes, for example, key figures that can be used to check compliance with defined threshold values. In justified cases, the BSI can prohibit the use of certain components.
Companies must act now - fines are imminent
The IT Security Act 2.0 imposes far-reaching obligations on numerous critical infrastructure companies, which can lead to serious consequences if disregarded. In particular, companies that have not previously belonged to the narrow circle of critical infrastructure operators will be subject to requirements that significantly extend the way in which cyber risks have been dealt with to date. The transition period for adaptation ends in May 2023, when companies that belong to the group of companies defined by the KRITIS Regulation must fully implement the IT-SiG 2.0. Companies must determine for themselves whether they are affected by the KRITIS Regulation. As part of the adjustments for the new IT Security Act 2.0, the associated catalog of fines has also been completely revised. In order for the BSI to fulfill its task, it has drastically increased fines at its disposal. These start with a breach of the duty to provide information and extend to inadequate implementation of the legal requirements for IT systems.
Adjustment of fines for non-compliance with the law
If, for example, the mandatory contact point cannot be reached, a fine of up to 100,000 euros can be imposed. If incidents are not reported or mandatory registrations are not carried out, fines of up to 500,000 euros can be imposed. The BSI can impose fines of up to 10 million euros for failure to provide evidence and can even impose fines of up to 20 million euros for violations of orders.
Guidance on the use of systems for attack detection (SzA)
The aim of this guidance document on the use of attack detection systems is to provide operators of critical infrastructures and auditing bodies with a point of reference for the individual implementation and auditing of precautions. Following the implementation of the 2nd IT Security Act, the BSIG now also explicitly mentions the use of attack detection systems in the new Section 8a (1a) BSIG. Such systems represent an effective measure for the (early) detection of cyber attacks and support damage reduction in particular.
You can download the SzA orientation guide here
Other laws and developments in the context of IT-SiG 2.0
The EU directives have been adopted at EU level, transposition into national law and the KRITIS umbrella law and IT Security Act 3.0 are under discussion. Here is an overview of upcoming laws and developments at EU and German level.
| Version | Status | Date | Actor |
| NIS 2 | Draft version | Dec 2020 | Commission |
| RCE (CER) | Draft version | Dec 2020 | Commission |
| IT Security Act 2.0 | Entry into force | May 2021 | Federal Council |
| NIS 2 | Consent NIS 2 | Nov 2022 | EU Parliament |
| RCE (CER) | Approval CER | Nov 2022 | EU Parliament |
| KRITIS umbrella law | Discussion | Nov 2022 | Press |
| NIS 2 | Assumption NIS 2 | Nov 2022 | Council of the EU |
| KRITIS umbrella law | Key points paper | Dec 2022 | Ministry of the Interior |
| KRITIS umbrella law | Legislation | 2023? | Germany |
| Ordinance on waste disposal | Legislation | H1 2023 | Germany |
| Ordinance UBI | Legislation | 2023? | Germany |
| IT Security Act 3.0 | Legislation | 2023? | Germany |
| NIS 2 | National implementation | until Aug 24 | Member states |
Conclusion
As a first step, companies should check whether they fall into the group defined by the CRITIS Regulation. If this is the case, a careful analysis of the current state of IT security in the company should be carried out in order to respond with suitable measures. In any case, companies need to familiarize themselves with the law and its requirements.
Sources:
BSI: https://www.bsi.bund.de/DE/Das-BSI/Auftrag/Gesetze-und-Verordnungen/IT-SiG/2-0/it_sig-2-0_node.html
Guidance on the use of attack detection systems : https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/KRITIS/oh-sza.html
