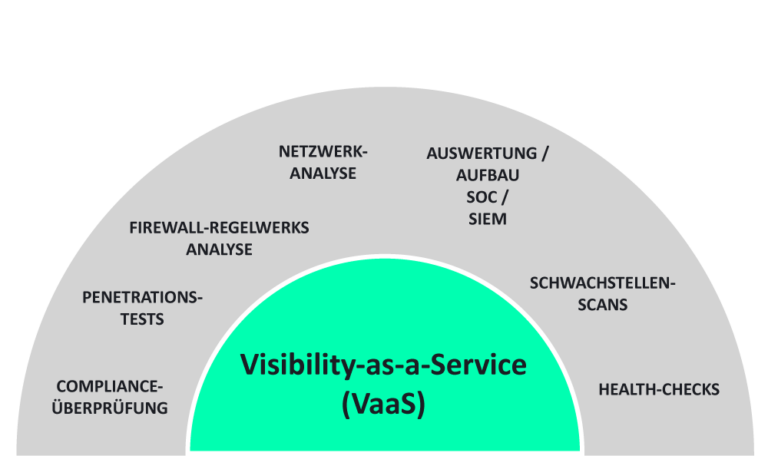
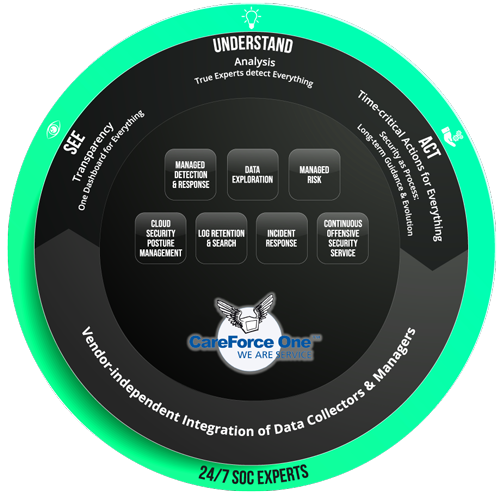
Visibility as a Service (VaaS)
Visibility-as-a-Service (VaaS) ist ein wesentlicher Bestandteil unserer CareForce One Dienstleistungsmarke und ermöglicht einen umfassenden Einblick in Ihre Infrastruktur. Mit VaaS können potenzielle Schwachstellen und Hardwareprobleme innerhalb Ihrer Infrastruktur sorgfältig identifiziert werden. Dabei greifen wir auf spezielle Scans und eigene Tools zurück, um auch Ihre Firewall Gateways und Management Systeme detailliert zu überprüfen.
Damit sollen die primären Schutzziele der IT-Sicherheit – Vertraulichkeit, Integrität und Verfügbarkeit der Netzwerke erreicht werden. Auch in Hinblick auf IT-Gesetze, wie NIS-2, müssen Maßnahmen zur Vermeidung von Sicherheitsvorfällen etabliert und überprüft werden.