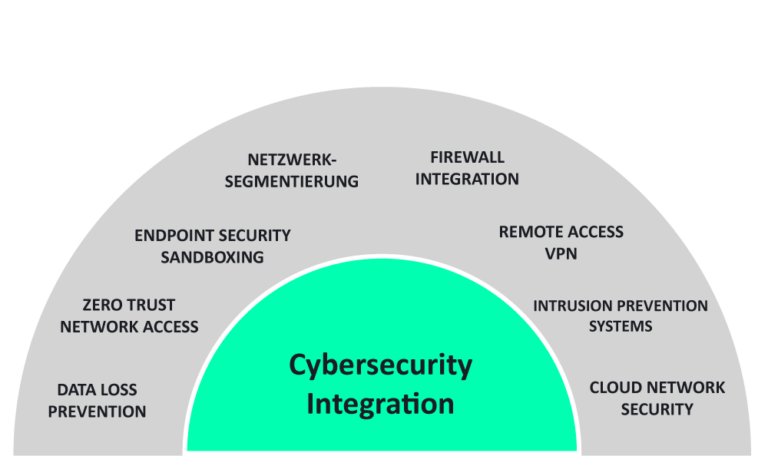
Cybersecurity integration
Cybersecurity integration supplements the organizational measures from certifications and internal guidelines. The content of the information security documents, classic paper security, is implemented through the operational implementation of various IT security measures. The focus here is on preventive measures that effectively protect the infrastructure, networks and end devices and ensure the confidentiality, integrity and availability of the IT infrastructure.